Yara
This section will cover Yara.
Table of Contents
- Introduction
- Yara Rule Basics
- Yara Rules
- Meta
- Strings
- Conditions
- Other Tools and Yara
- LOKI
- THOR Lite
- FENRIR
- Valhalla
- Creating Yara Rules with yarGen
Introduction
Yet Another Ridiculous Acronym (Yara) can be used to identify information based on both binary and textual patterns, such as hexadecimal and strings contained within a file.
https://github.com/virustotal/yara
Yara rules can be written to search for a specified string. Strings can be anything such as a IP address within malware to connect to a C2 server or a URL that downloads additional malware.
To install Yara, we can simply run sudo apt install yara. Note that different Linux distributions may have different commands or package names.
Yara Rule Basics
Yara uses a proprietary language to write rules. It can be trivial to pick up but hard to master as the rules written are only as effective as our understanding of the patterns that we are searching for. Yara uses the .yar extension for rule files.
When using the yara command, it requires two arguments to be valid:
- The rule file we created.
- The name of the target (e.g., file, directory, or process ID) to scan.
An example will be where we have a rule file named my-yara-rule.yar and the directory that we want to search will be mydir.
yara my-yara-rule.yar mydir
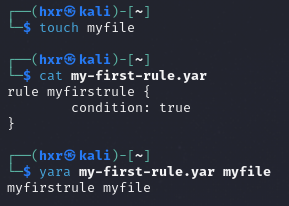
When writing rules, each rule must have a name and condition. The following is an example of a Yara rule.
rule myfirstrule {
condition: true
}
Breakdown:
myfirstrule- The rule name.condition: true- The condition to match for.
The above rule will match if the condition is true. In other words, match everything. An example will be where a new file is created (e.g. myfile). We can use the following command to search for instances of myfile using the created rule by specifying the created file as the target.
yara my-yara-rule.yar myfile
When there is a match, Yara will return the rule name. An example will be the following screenshot where myfirstrule myfile is returned as the file exists.
To assign variables in Yara rules, we can use a dollar sign ($) followed by the variable name.
rule namecheck {
strings:
$name = "stux"
condition: $name
}
The above rule will match all instances of the stux string as the string value is being used as the condition.
Yara Rules
When writing Yara rules, we can use different conditions (keywords) to match patterns.
Some keywords are:
- Meta
- Strings
- Conditions
To view more keywords that can be used, visit the official documentation:
https://yara.readthedocs.io/en/stable/writingrules.html
The following graphic depicts the anatomy of a Yara rule.
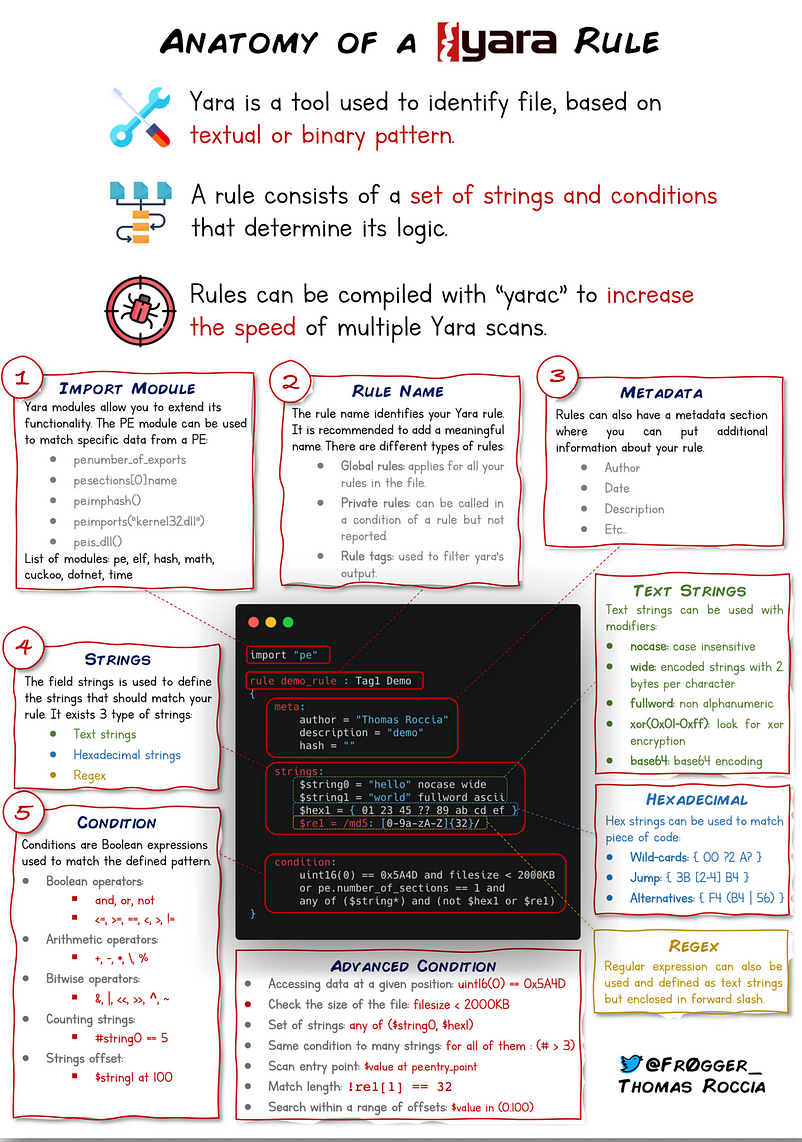
Meta
This section of a Yara rule is reserved for descriptive information by the author. An example will be using the description keyword which can be used to summarise the purpose of the rule.
rule mytestrule {
meta:
description = "my rule desc"
score = 60
date = "2025/01/11"
strings:
$file_name = "maldown"
condition:
$file_name
}
Anything written in this section does not influence the rule itself. This is similar to adding comments when coding.
Strings
Strings can be used to search for specific text, hexadecimal, patterns, and more in files or programs. An example will be where we are looking for the string stux in the target directory.
rule malware_check {
strings:
$mal_name = "stux"
condition:
$mal_name
}
The above rule will match all instances of the string stux as we are using the $mal_name variable as the condition.
Multiple strings can also be specified. To match any of the strings (one or more hits), we can use the any of them condition.
rule malware_check {
strings:
$mal_name1 = "stux"
$mal_name2 = "trojan"
$mal_name3 = "shell"
condition:
any of them
}
The above rule will match all instances of the string stux, trojan, or shell in the specified target.
Conditions
There are many different conditions that can be used such as operators. The following table will display some common operators that can be used. Conditions can also be combined using operators such as and or or.
| Operator | Description |
|---|---|
== | Equal to. |
< | Less than. |
<= | Less than or equal to. |
> | Greater than. |
>= | Greater than or equal to. |
!= | Not equal to. |
| contains | String contains the specified substring. |
| startswith | String starts with the specified substring. |
| not | Logical NOT |
| and | Logical AND |
| or | LOGICAL OR |
| true | Boolean |
| false | Boolean |
More conditions can be found at the official documentation:
https://yara.readthedocs.io/en/stable/writingrules.html#conditions
An example will be a rule that matches a specified string and file size.
rule string_size_check {
strings:
$str1 = "stux"
condition:
$str1 and filesize > 200KB
}
The above rule will match if the target contains the string str and has a file size greater than 200KB.
Other Tools and Yara
There are many resources that can be used with Yara. Some examples are:
- LOKI
- THOR Lite
- FENIRIR
LOKI
LOKI is an open-source indicator of compromise (IOC) scanner created by Florian Roth.
https://github.com/Neo23x0/Loki
LOKI can be downloaded on both Windows and Linux systems. Detection is based on 4 methods:
- File Name IOC Check
- Yara Rule Check
- Hash Check
- C2 Back Connect Check
Additional checks that LOKI uses can be found on the GitHub README.md.
https://github.com/Neo23x0/Loki/blob/master/README.md
To use LOKI, simply clone the GitHub repository and use python loki.py. To scan the a directory, we can use the -p /path/to/dir/ option with LOKI.
THOR Lite
THOR and THOR Lite is a multi-platform IOC and Yara scanner created by Florian Roth. It is able to work on Linux, Windows, and macOS.
https://www.nextron-systems.com/thor-lite/
A feature of THOR Lite is that it throttles its scan to limit CPU resource usage. Note that THOR is geared towards enterprise customers while THOR Lite is the free version.
FENRIR
FENRIR is a bash script that can run on almost any system capable of running bash.
https://github.com/Neo23x0/Fenrir
Valhalla
Valhalla is an online Yara feed created and hosted by Nextron-Systems (Florian Roth).
https://www.nextron-systems.com/valhalla/
Valhalla allows us to conduct searches based on different keywords such as the MITRE ATT&CK technique, SHA256 hash, or rule name.
When searching for a rule, we are presented the rule, a brief description, the date created, and a reference link.
Creating Yara Rules with yarGen
yarGen, created by Florian Roth using Python, is a tool that can take an input file and create a rule for it while excluding all the goodware strings and opcode (strings that appear in good, non-malicious files).
https://github.com/Neo23x0/yarGen
yarGen comes with a database of goodware strings and opcode as ZIP archives that have to be extracted before the first use.
To update the database, we can use the following command.
python3 yarGen.py --update
This process will update the database and will take a few minutes.
Once it has been updated, we can create a detection rule by specifying the directory that we want to create detection rules for.
python3 yarGen.py -m /path/to/dir --excludegood -o /path/to/output/rule.yar
Command breakdown:
-m /path/to/dir- Specify the input directory to create the Yara rule for.--excludegood- Force to exclude all goodware strings (may increase false positives if left included).-o /path/to/output/rule.yar- Specify the path and file name to save the rule to.
An example:
python3 yarGen.py sus-files --excludegood -o myrule.yar
The above command will create a rule to detect any malicious files in the sus-files directory. The rule is then saved to a file named myrule.yar.