SMTP - Simple Mail Transfer Protocol
This section will cover ways to enumerate Simple Mail Transfer Protocol (SMTP).
Table of Contents
- Overview
- Default Configuration
- HELO/EHLO
- VRFY
- Sending an Email
- Dangerous Settings
- Enumerating SMTP
- Nmap
Overview
Simple Mail Transfer Protocol (SMTP) is used to send emails in an IP network. It can be used between an email client and an outgoing mail server or between two SMTP servers. SMTP is often used together with Internet Message Access Protocol (IMAP) or Post Office Protocol version 3 (POP3), which can fetch and send mails.
The default port for SMTP is TCP port 25. However, newer SMTP servers also use other ports such as TCP port 587.
TCP port 587 is used to receive mail from authenticated users/servers, usually using the STARTTLS command to switch the existing plaintext connection to an encrypted connection.
SMTP works unencrypted without further measures and transmits all commands, data, or authentication information over the network in plaintext. To prevent unauthorised access of reading the data, SMTP is used in conjunction with SSL/TLS encryption. In some circumstances, a server uses a port other than the standard TCP port 25 for the encrypted connection. For example, TCP port 465.
Most modern SMTP servers also support protocol extension Extended SMTP (ESMTP) with SMTP-Auth to prevent spam using authentication mechanisms. After sending an email, the SMTP client, also known as Mail User Agent (MUA), converts it into a header and a body and uploads both to the SMTP server. Then, a Mail Transfer Agent (MTA), the software basis for sending and receiving emails, checks the email for size and spam and then stores it.
To relieve the MTA, it is occasionally preceded by a Mail Submission Agent (MSA), which checks the validity, such as the origin of the email. The MSA is also called a relay server. These are very important later on attacks such as open relay attacks can be carried out due to misconfigurations in SMTP servers. The MTA then searches the DNS for the IP address of the recipient mail server.
On arrival at the destination SMTP server, the data packets are reassembled to form a complete email. From there, the Mail Delivery Agent (MDA) transfers it to the recipient's mailbox.
The below screenshot shows the order on how mail is sent and receive.

SMTP has 2 disadvantages inherent to the network protocol:
- It does not return a usable delivery confirmation. Although the specifications of the protocol provide for this type of notification, its formatting is not specified by default.
- Users are not authenticated when a connection is established, and the sender of an email is therefore unreliable. As a result, open SMTP relays are often misused to send spam email. However, there are security techniques in place such as DKIM and SPF to help prevent misuse.
For this purpose, an extension for SMTP has been developed called ESMTP. Generally when talking about SMTP, it is referring to ESMTP. It uses TLS, which is done after the EHL0 command by sending STARTTLS. This initialises the SSL-protected SMTP connection. Now AUTH PLAIN extension for authentication can be used safely.
Default Configuration
Each SMTP server can be configured in many ways. However, there are differences because the SMTP server is only responsible for sending and forwarding emails.
The default configuration can be found in the /etc/postfix/main.cf file. The below table will list some commands for SMTP and their description.
| Command | Description |
|---|---|
| AUTH PLAIN | AUTH is a service extension used to authenticate the client. |
| HELO | The client logs in with its computer name and starts the session. |
| MAIL FROM | The client names the email sender. |
| RCPT TO | The client names the email recipient. |
| DATA | The client initiates the transmission of the email. |
| RSET | The client aborts the initiated transmission but keeps the connection with the server. |
| VRFY | The client checks if a mailbox is available for message transfer. |
| EXPN | The client checks if a mailbox is available for messaging with this command. |
| NOOP | The client requests a response from the server to prevent disconnection due to time-out. |
| QUIT | The client terminates the connection. |
To interact with the SMTP server, we can use telnet to initialise a TCP connection with the server. The actual initialisation of the session is done with the command as mentioned above (HELO or EHELO).
telnet 10.10.1.20 25
Command breakdown:
10.10.1.20- Specify the server IP address.25- Specify the port to connect to.
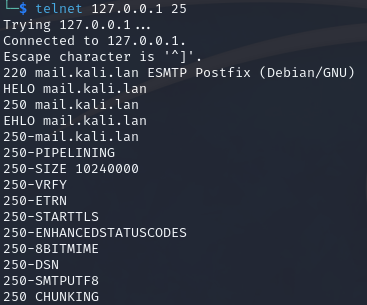
HELO/EHLO
We can use the HELO or EHLO command after connecting using Telnet to initialise the connection.
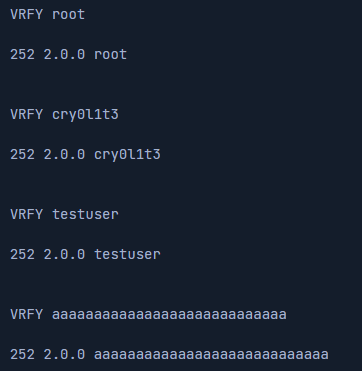
VRFY
We can use the command VRFY to enumerate existing users on the system. However, this does not always work. Depending on how the SMTP server is configured, it may issue code 252 and confirm that a user does not exist. A list of codes can be found at https://serversmtp.com/smtp-error/.
Note: We may need to work through a web proxy sometimes. To connect the web proxy to the SMTP server, we can use the command CONNECT 10.10.10.1:25 HTTP/1.0.
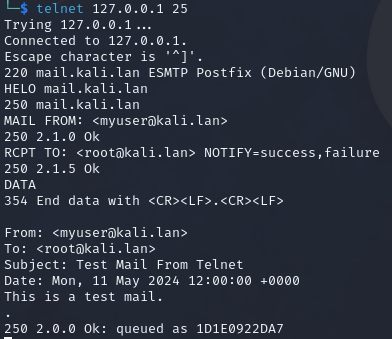
Sending an Email
We can send an email by using the MAIL FROM: <EMAIL@HERE.TLD>, RCPT TO: <EMAIL@HERE.TLD>, and DATA. Do note that we will have to initialise a connection using HELO or EHLO before we can use the mentioned commands.
The mail header is the carrier of a large amount of interesting information in an email. Among other things, it provides information about the sender, recipient, the time of sending and arrival, the stations the email passed on its way, and the content and format.
Some of these information is mandatory, such as sender information and when the email was created. Other information are optional. However, the email header does not contain any information necessary for technical delivery. The structure of an email header is defined in RFC5322.
Dangerous Settings
To prevent the sent emails from being filtered as spam, the sender can use a relay server that the recipient trusts. A relay server is a SMTP server that is known and verified by others. As a rule, the sender must authenticate to the relay server before using it.
Often, administrators have no overview of which IP ranges to allow. This results in a misconfiguration where every IP address is allowed. This allows an attacker to send fake emails or spoof emails and read them.
Misconfiguration:
mynetworks = 0.0.0.0/0
Enumerating SMTP
There are several tools we can use to enumerate SMTP. One of such tools is Nmap.
Nmap
We can use the NSE and the smtp-commands which is included in the default script which uses the EHLO command to list all possible commands that can be executed on the target SMTP server.
sudo nmap -sC -sV -p25 10.42.0.1
Command breakdown:
-sC- Specify Nmap to use default scripts.-sV- Specify to scan the version of the services.-p25- Specify the port to scan.10.42.0.1- Specify the target IP address.
We can also use other scripts such as the smtp-open-relay script to identify if the target is an open relay using 16 different tests. We can use the -v flag to see which tests the script is running.
sudo nmap -p25 --script smtp-open-relay -v 10.42.0.1
Command breakdown:
-p25- Specify the port to scan.--script smtp-open-relay- Specify to use thesmtp-open-relayNSE script.-v- Enable verbose mode.10.42.0.1- Specify the IP address of the target.
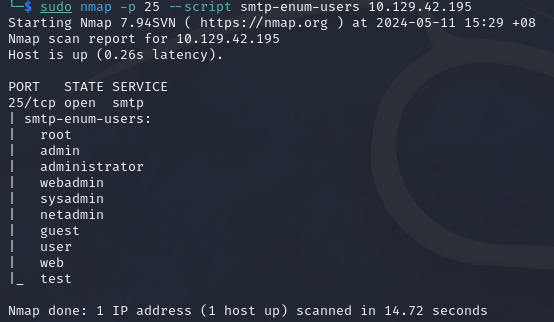
We can also enumerate users on the server with the smtp-enum-users NSE script.
nmap -p 25 --script smtp-enum-users 10.42.0.1
Command breakdown:
-p 25- Specify the port to scan.--script smtp-enum-users- Specify to use thesmtp-enum-usersscript.10.129.42.195- Specify the target IP address.